Breadcrumb
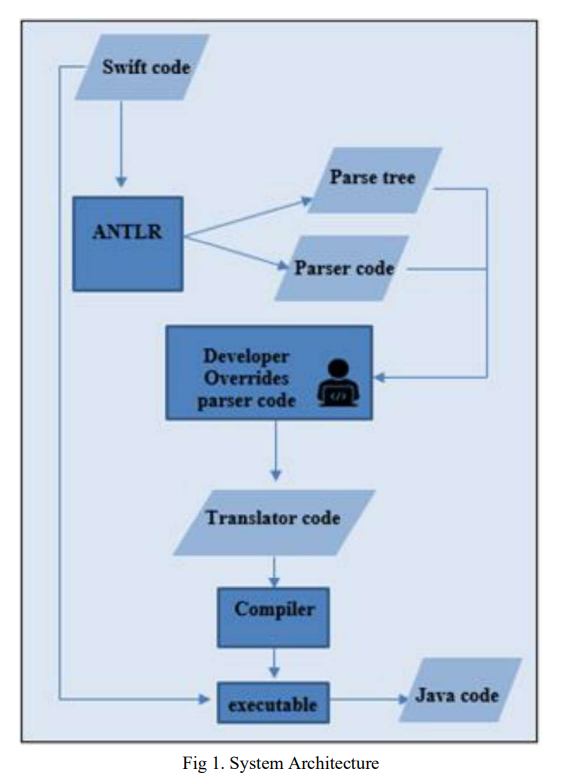
Trans-Compiler based Mobile Applications code converter: Swift to java
Numerous commercial tools like Xamarin, React Native and PhoneGap utilize the concept of cross-platform mobile applications development that builds applications once and runs it everywhere opposed to native mobile app development that writes in a specific programming language for every platform. These commercial tools are not very efficient for native developers as mobile applications must be written in specific language and they need the usage of specific frameworks. In this paper, a suggested approach in TCAIOSC tool to convert mobile applications from Android to iOS is used to develop the
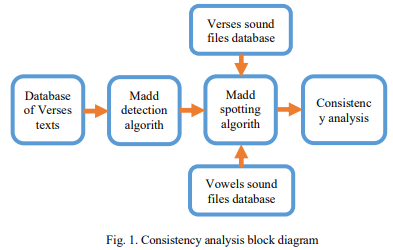
Consistency Analysis of Madd rules in the Holy Quran
A consistency analysis is performed for one of the famous Tajweed rules in the Holy Quran - Madd rules. They are tested on records of one of the famous reference reciters - Sheikh El-Hosary-to find a consistent boundaries and to evaluate the performance of other new learners. A vowel detection algorithm is used to detect the duration of the detected Madd patterns. This algorithm was applied on a dataset of 105 minutes of Quranic records of Sheikh El-Hosary. The consistency result is found to be normally distributed with a mean of 0.379 second of one movement time of Madd and standard deviation
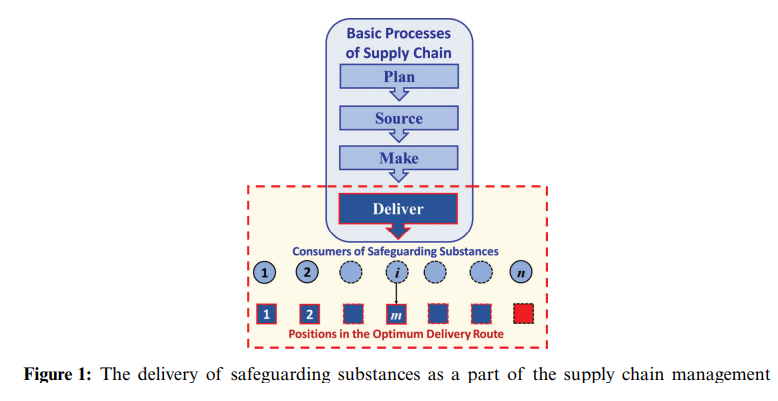
Managing Delivery of Safeguarding Substances as a Mitigation against Outbreaks of Pandemics
The optimum delivery of safeguarding substances is a major part of supply chain management and a crucial issue in the mitigation against the outbreak of pandemics. A problem arises for a decision maker who wants to optimally choose a subset of candidate consumers to maximize the distributed quantities of the needed safeguarding substances within a specic time period. A nonlinear binary mathematical programming model for the problem is formulated. The decision variables are binary ones that represent whether to choose a specic consumer, and design constraints are formulated to keep track of the

The overexpression of DNA repair genes in invasive ductal and lobular breast carcinomas: Insights on individual variations and precision medicine
In the era of precision medicine, analyzing the transcriptomic profile of patients is essential to tailor the appropriate therapy. In this study, we explored transcriptional differences between two invasive breast cancer subtypes; infiltrating ductal carcinoma (IDC) and lobular carcinoma (LC) using RNA-Seq data deposited in the TCGA-BRCA project. We revealed 3854 differentially expressed genes between normal ductal tissues and IDC. In addition, IDC to LC comparison resulted in 663 differentially expressed genes. We then focused on DNA repair genes because of their known effects on patients'
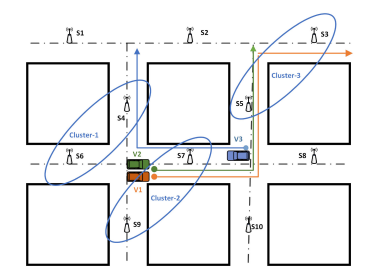
Mobility-Aware Edge Caching for Minimizing Latency in Vehicular Networks
This work proposes novel proactive caching schemes for minimizing the communication latency in Vehicular Ad Hoc Networks (VANETs) under freeway and city mobility models. The main philosophy that underlies these schemes is to exploit information that may be available a priori for vehicles' demands and mobility patterns. We consider two paradigms: cooperative, wherein multiple Roadside Units (RSUs) collaborate to expedite the transfer of information to the intended user, and non-cooperative, wherein each RSU operates independently of other RSUs in the network. To develop the proposed schemes
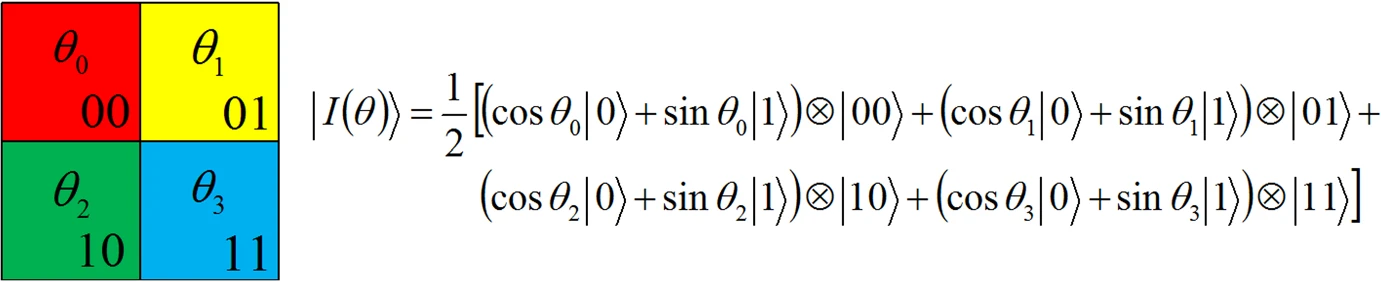
QIRHSI: novel quantum image representation based on HSI color space model
We present QIRHSI, a novel quantum image representation method based on the HSI color space model. QIRHSI integrates the advantages of the Flexible Representation of Quantum Images (FRQI) model and the Novel Enhanced Quantum Representation (NEQR) model. On the one hand, the proposed QIRHSI model is better suited for the image processing related to intensity information via binary qubit sequence than multi-channel representation for quantum image (MCQI) (multi-channel FRQI). On the other hand, the QIRHSI model requires less storage space (10 qubits) in the hue and saturation channels, compared
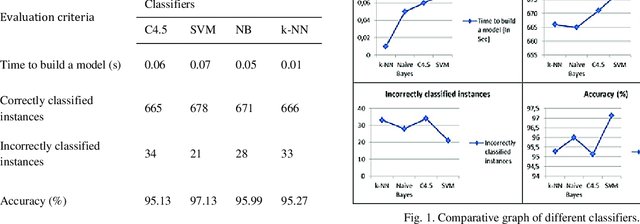
Using machine learning algorithms for breast cancer diagnosis
There are many cancer patients, especially breast cancer patients as it is the most common type of cancer. Due to the huge number of breast cancer patients, many breast cancer-focused hospitals aren't able to process the huge number of patients and might expose some women to late stages of cancer. Thus, the automation of the process can help these hospitals in speeding up the process of cancer detection. In this paper, the authors test several machine learning models such as k-nearest neighbours (KNN), support vector machine (SVM), and artificial neural network (ANN). They then compare their
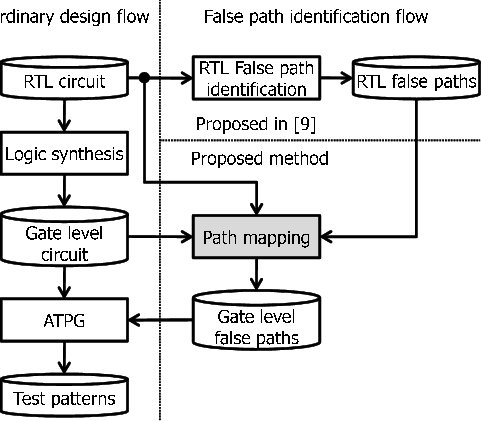
Utilization of Machine Learning In RTL-GL Signals Correlation
Verification is an important part of the Electronic Design Automation (EDA) design flow which currently takes a considerable amount of time. During the synthesis process, Different optimizations are done to the Register-Transfer-Level (RTL) code to optimize the power, area, and speed of the circuit. These optimizations result in changes in the names of signals at the gate level. Automatic signal mapping can improve the verification process and can be used to guide functional verification activities between the two presentations using (Clock domain crossing (CDC) analysis in RTL, Gate Level CDC
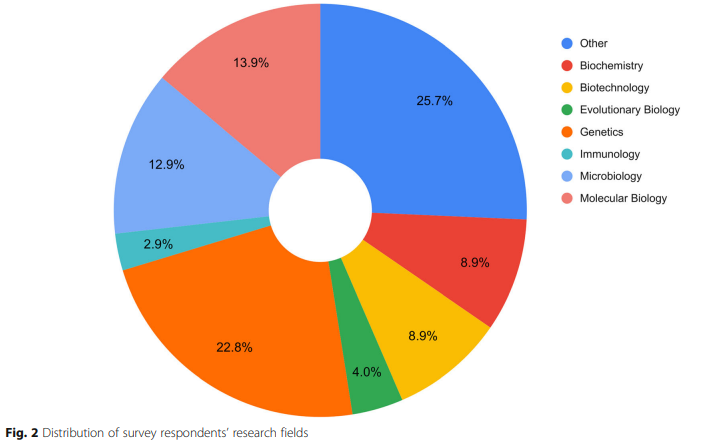
The H3ABioNet helpdesk: An online bioinformatics resource, enhancing Africa's capacity for genomics research
Background: Currently, formal mechanisms for bioinformatics support are limited. The H3Africa Bioinformatics Network has implemented a public and freely available Helpdesk (HD), which provides generic bioinformatics support to researchers through an online ticketing platform. The following article reports on the H3ABioNet HD (H3A-HD)'s development, outlining its design, management, usage and evaluation framework, as well as the lessons learned through implementation. Results: The H3A-HD evaluated using automatically generated usage logs, user feedback and qualitative ticket evaluation
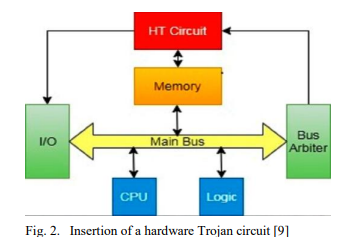
Securing Hardware from Malicious Attacks
Hardware security is considered a major design and manufacturing target area with a broad range of research and development topics such as protection of intellectual property (IP), metering of hardware, detection of hardware Trojans, and a lot of other topics. This paper discusses Trojan realization in integrated circuits (ICs), as well as the possible security measures, also exploring the usage of the 3-D integration in hardware security where additional hardware can be mounted after fabrication to foster secure execution just for those systems which need it. © 2021 IEEE.
Pagination
- Previous page ‹‹
- Page 31
- Next page ››
