Breadcrumb
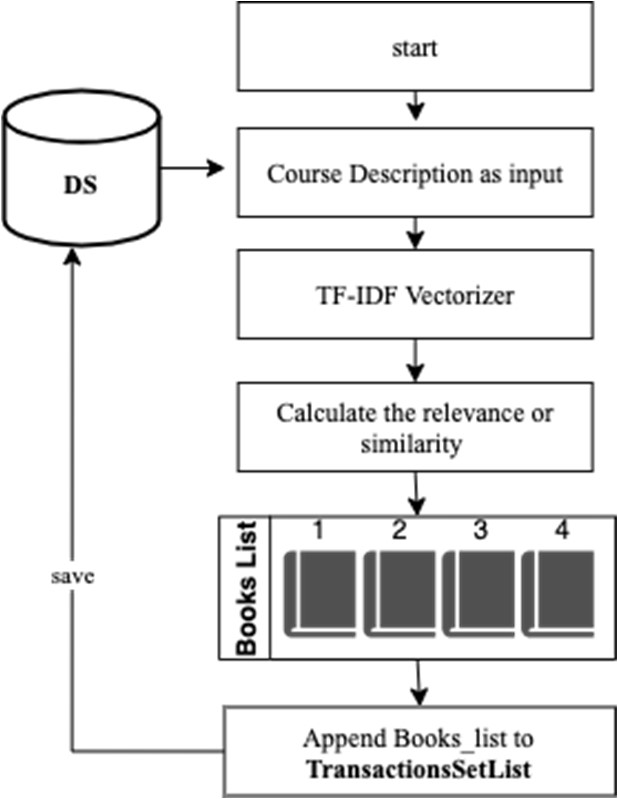
A HYBRID RECOMMENDER FRAMEWORK FOR SELECTING A COURSE REFERENCE BOOKS
Recommender systems are receiving great attention these days, as various researchers and major companies are conducting continuous research in this field. Companies like Google and Amazon have provided different effective models for video recommendation systems, but the educational field is poorly studied as other researchers explained. Different researchers proposed various approaches showing the challenges related to recommender systems and have proposed various effective recommender systems. This paper aims to propose a hybrid recommender framework that can recommend educational courses'
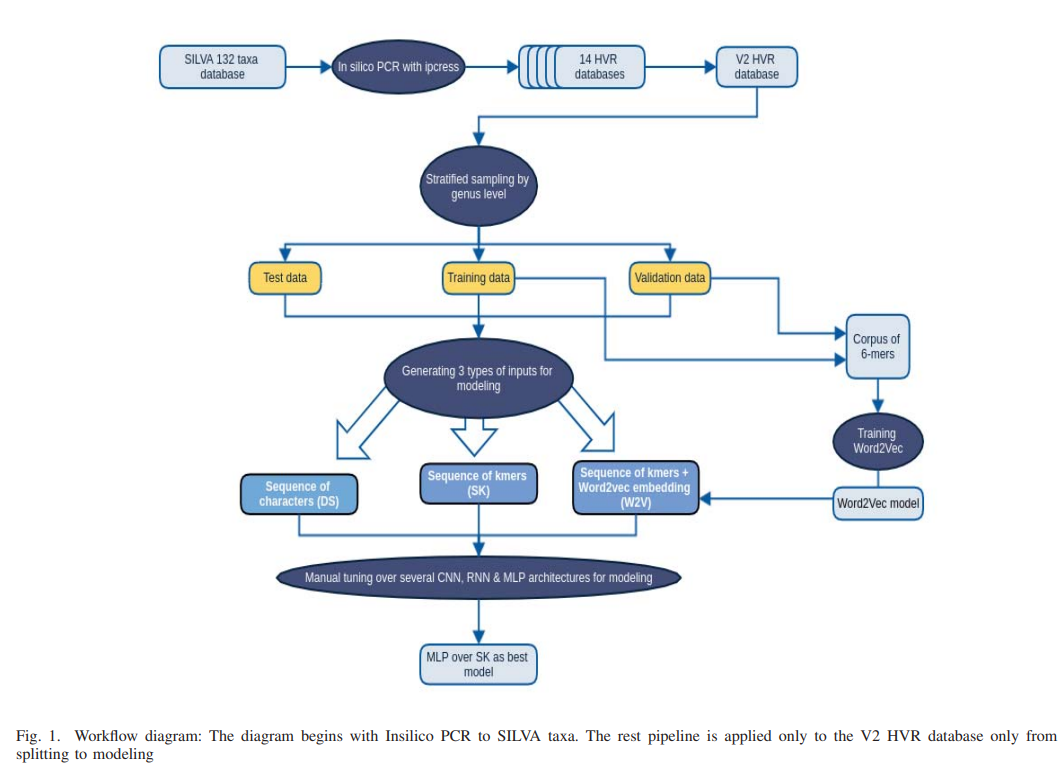
AmpliconNet: Sequence Based Multi-layer Perceptron for Amplicon Read Classification Using Real-time Data Augmentation
Taxonomic assignment is the core of targeted metagenomics approaches that aims to assign sequencing reads to their corresponding taxonomy. Sequence similarity searching and machine learning (ML) are two commonly used approaches for taxonomic assignment based on the 16S rRNA. Similarity based approaches require high computation resources, while ML approaches dont need these resources in prediction. The majority of these ML approaches depend on k-mer frequency rather than direct sequence, which leads to low accuracy on short reads as k-mer frequency doesnt consider k-mer position. Moreover
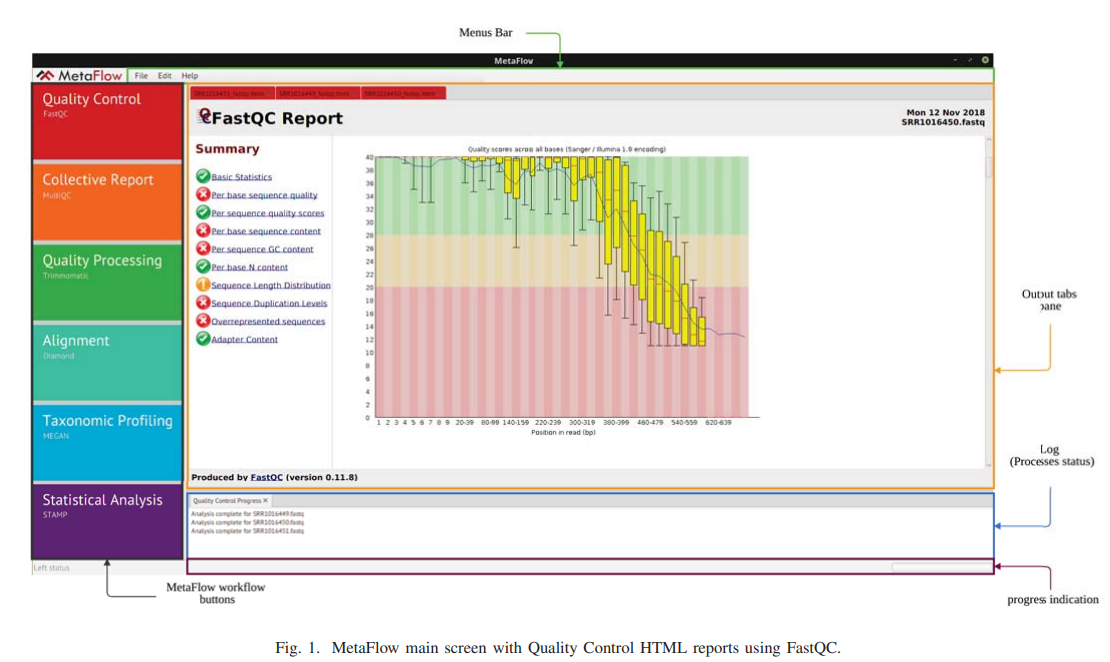
MetaFlow: An interactive user-friendly workflow for automated analysis of whole genome shotgun sequencing metagenomic data
Metagenomics is a rapidly emerging field that is concerned with the study of microbial communities 'microbiomes' on both levels of taxonomic classification and functional annotation. Targeted amplicon (16S rRNA) and whole genome shotgun (WGS) sequencing are the two main sequencing strategies in metagenomics. As amplicon sequencing provides a cheap way to classify the composition of a microbial community, it lacks the ability to identify microbial genes and annotate its corresponding functions. On the other hand, WGS sequencing allows further investigation of the complete genomes with all
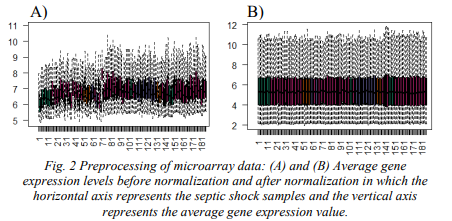
Studying Genes Related to the Survival Rate of Pediatric Septic Shock
Pediatric septic shock is generally considered as a devastating clinical syndrome that can lead to tissue damage and organ failure due to the over exaggerated immune response to an infection. Therefore, in this paper, we attempted to early identify the clinical course of such disease with the aid of peripheral blood T-cells of 181 pediatric patients who admitted to Intensive Care Unit (ICU), Accordingly, 34 differential expressed genes have been identified as biological genetic biomarkers. Minimum redundancy and maximum relevance feature selection strategy has been proposed for the discovery
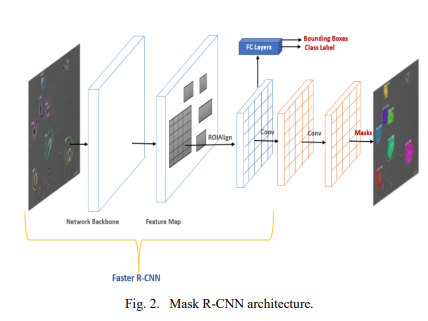
Instance Segmentation of 2D Label-Free Microscopic Images using Deep Learning
The precise detection and segmentation of cells in microscopic image sequences is an essential task in biomedical research, such as drug discovery and studying the development of tissues, organs, or entire organisms. However, the detection and segmentation of cells in phase contrast images with a halo and shade-off effects is still challenging. Lately, Mask Regional Convolutional Neural Network (Mask R-CNN) has been introduced for object detection and instance segmentation of natural images. This study investigates the efficacy of the Mask R-CNN to instantly detect and segment label-free

Robust Background Template for Saliency Detection
In this paper, we propose an effective saliency detection method based on dense and sparse representation in-terms of an optimized background template. Firstly, the input image is divided into compact and uniform super-pixels. Then, the optimized background template is produced by introducing boundary conductivity measurement to improve the dense and sparse representation of the image's super-pixels in terms of the optimized background, where the reconstruction error represents a saliency measure. Based on the optimized template, two saliency maps are generated by dense and sparse
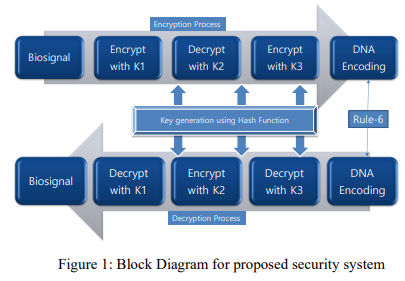
An E-health System for Encrypting Biosignals Using Triple-DES and Hash Function
This Electronic Health (E-Health) is a broad expression that enables the communication between healthcare professionals in handling patient information through the cloud. Exchanging medical data over the public cloud requires securing transferring for the data that's direct many researchers in proposing different secure schemes to enable users to handle data safely without hacking or alternating. In this study, one of the most common encryption algorithms called Triple Data Encryption Standard (Triple-DES) has been implemented with the aid of the hash function and DNA cryptography base to
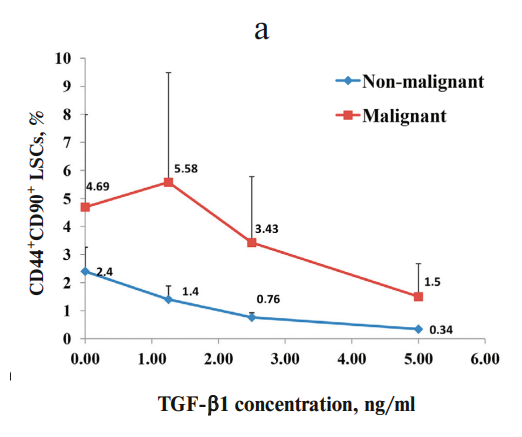
Role of TGF-β1 and C-Kit Mutations in the Development of Hepatocellular Carcinoma in Hepatitis C Virus-Infected Patients: in vitro Study
Transforming growth factor beta (TGF-β) acts as a tumor-suppressing cytokine in healthy tissues and non-malignant tumors. Yet, in malignancy, TGF-β can exert the opposite effects that can promote proliferation of cancer cells. C-Kit plays a prominent role in stem cell activation and liver regeneration after injury. However, little is known about the cross-talk between TGF-β and C-Kit and its role in the progression of hepatocellular carcinoma (HCC). Here, we studied the effect of increasing doses of TGF-β1 on CD44+CD90+ liver stem cells (LSCs) and C-Kit gene expression in malignant and
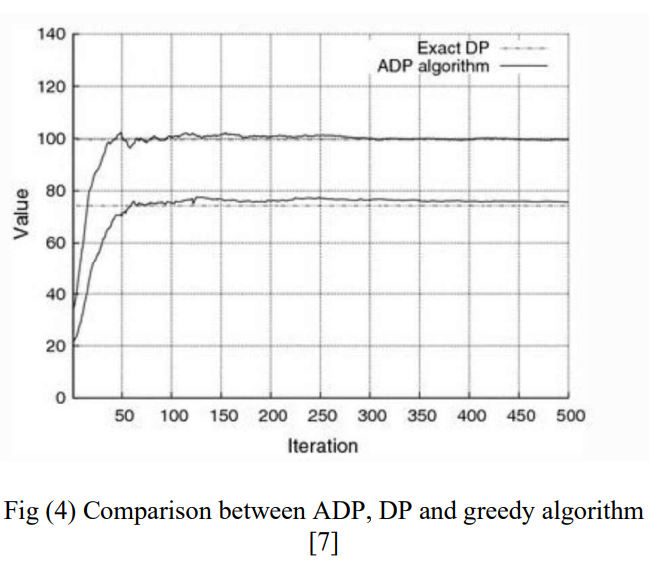
Dynamic Programming Applications: A Suvrvey
Dynamic programming is a mathematical optimization first invented in 1950s and lived till our times to make optimizations and reduce complexity in several different fields like bioinformatics, Electric vehicles, energy consumption, medical field and much more as a proof of being a powerful technique. In this paper, the various fields and aspects in which Dynamic programming has a significant contribution are surveyed. © 2020 IEEE.
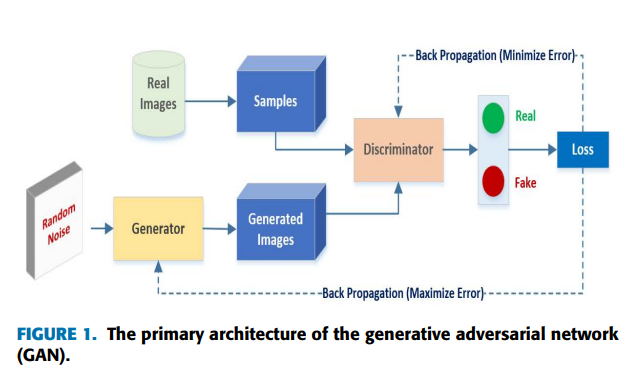
License Plate Image Analysis Empowered by Generative Adversarial Neural Networks (GANs)
Although the majority of existing License Plate (LP) recognition techniques have significant improvements in accuracy, they are still limited to ideal situations in which training data is correctly annotated with restricted scenarios. Moreover, images or videos are frequently used in monitoring systems that have Low Resolution (LR) quality. In this work, the problem of LP detection in digital images is addressed in the images of a naturalistic environment. Single-stage character segmentation and recognition are combined with adversarial Super-Resolution (SR) approaches to improve the quality
Pagination
- Previous page ‹‹
- Page 15
- Next page ››
