Breadcrumb
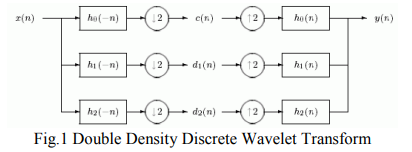
Bivariate Double Density Discrete Wavelet for Enhanced Image Denoising
Image denoising is of paramount importance in image processing. In this paper, we propose a new design technique for the design of Double density Discrete Wavelet Transform (DD DWT) AND DD CWT filter bank structure. These filter banks satisfy the perfect reconstruction as well as alias free properties of the DWT. Next, we utilized this filter bank structure in image denoising. Our denoising scheme is based on utilizing the interscale correlation/interscale dependence between wavelet coefficients of a DD DWT of the noisy image. This is known as the Bivariate Shrinkage scheme. More precisely, we
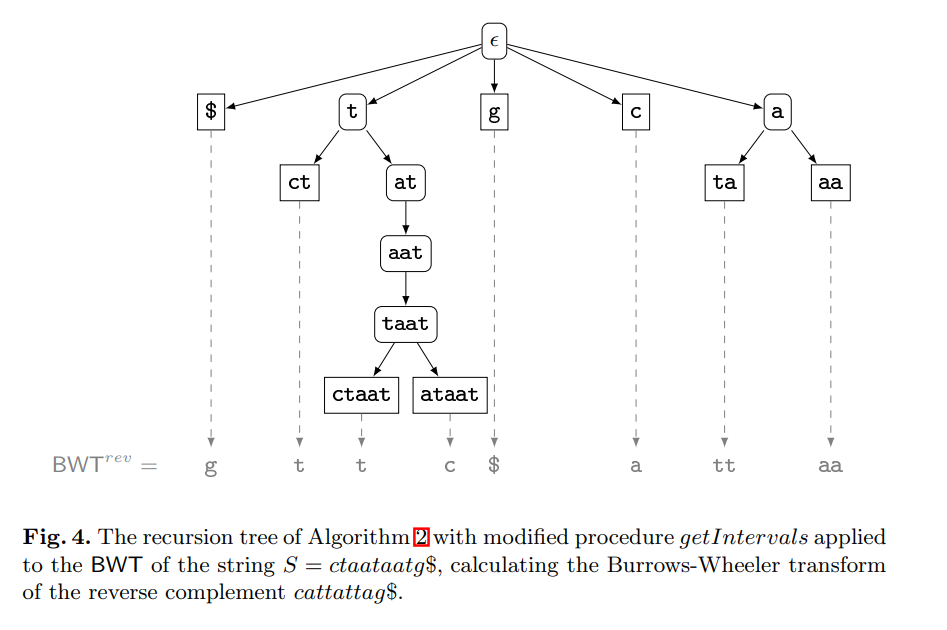
Computing the burrows-wheeler transform of a string and its reverse
The contribution of this paper is twofold. First, we provide new theoretical insights into the relationship between a string and its reverse: If the Burrows-Wheeler transform (BWT) of a string has been computed by sorting its suffixes, then the BWT and the longest common prefix array of the reverse string can be derived from it without suffix sorting. Furthermore, we show that the longest common prefix arrays of a string and its reverse are permutations of each other. Second, we provide a parallel algorithm that, given the BWT of a string, computes the BWT of its reverse much faster than all
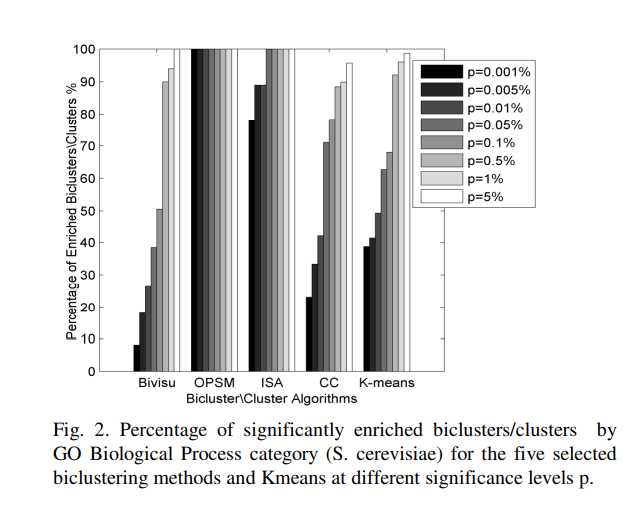
An automatic gene ontology software tool for bicluster and cluster comparisons
We propose an Automatic Gene Ontology (AGO) software as a flexible, open-source Matlab software tool that allows the user to easily compare the results of the bicluster and cluster methods. This software provides several methods to differentiate and compare the results of candidate algorithms. The results reveal that bicluster/cluster algorithms could be considered as integrated modules to recover the interesting patterns in the microarray datasets. The further application of AGO could to solve the dimensionality reduction of the gene regulatory networks. Availability: AGO and help file is
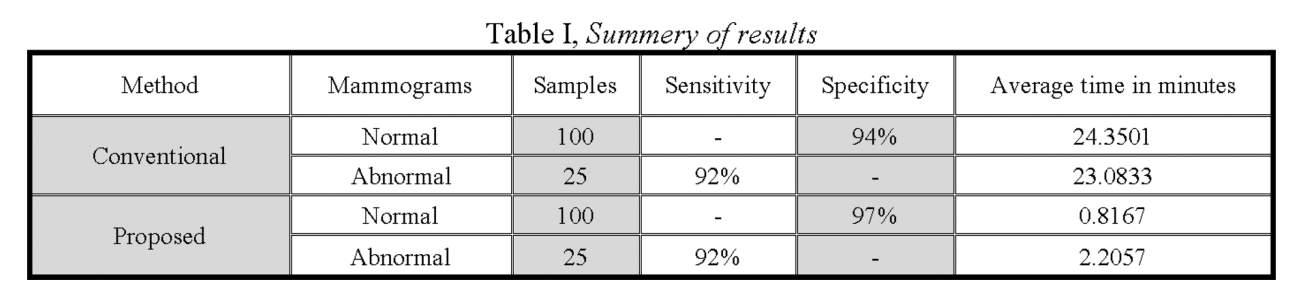
Fast fractal modeling of mammograms for microcalcifications detection
Clusters of microcalcifications in mammograms are an important early sign of breast cancer in women. Comparing with microcalcifications, the breast background tissues have high local self-similarity, which is the basic property of fractal objects. A fast fractal modeling method of mammograms for detecting the presence of microcalcifications is proposed in this paper. The conventional fractal modeling method consumes too much computation time. In the proposed method, the image is divided into shade (homogeneous) and non-shade blocks based on the dynamic range and only the non-shade blocks are
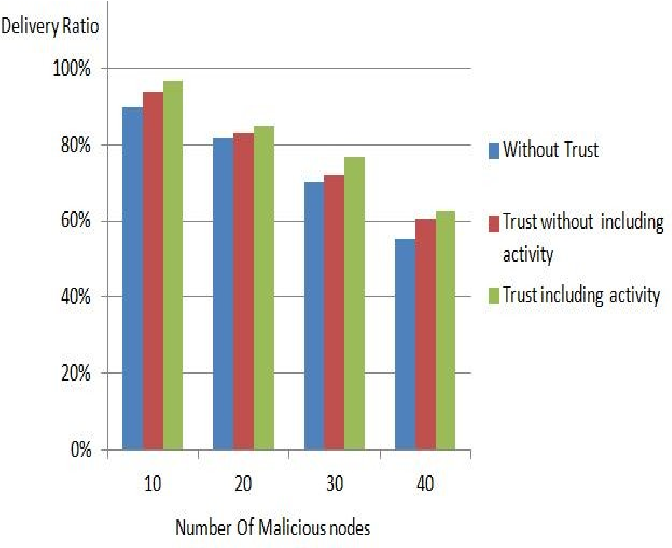
A novel proximity based trust model for opportunistic networks
Trust should be earned. This is a famous quote that we use everyday implicitly or explicitly. Trust often is an inherent characteristic of our daily life, but in the digital community and between devices how can we represent trust? Since our mobile and digital devices became our confidants, we cannot share the information embedded in these devices with other devices without establishing trust. Hence, in this research a proximity based trust model based on Homophily principle is proposed. Earlier social studies have shown that people tend to have similarities with others in close proximity. In
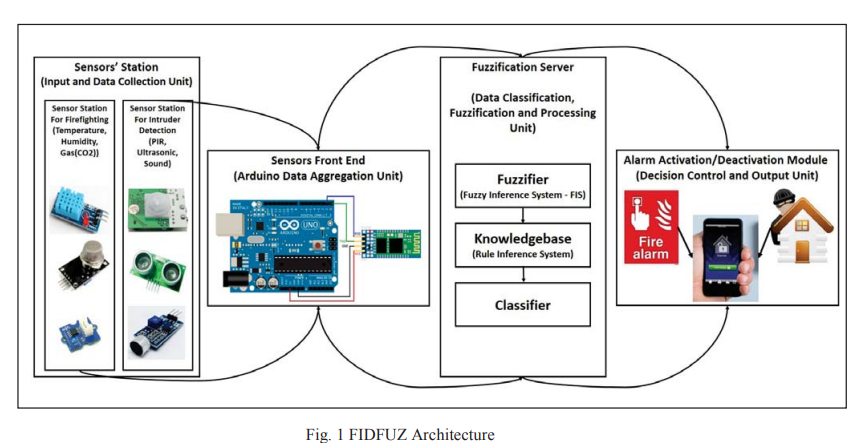
Design and implementation of robust firefighting/intruder detection system using fuzzy logic decision control (FIDFUZ)
This research focuses on using quantifiable methods for using the IoT as a main support to firefighting/intruder detection. From our research, we have found numerous researches associated to supplying remote services by means of portable sensors and communication technologies. We represent in our research a unique Smart Firefighting/lntruder Detection System with the support of Fuzzy Logic Decision Control (FIDFUZ). The projected system has an innovative value which is the Fuzzy Logic Decision Support System application that deals with the predicted inaccuracy and the doubt in the sensor's
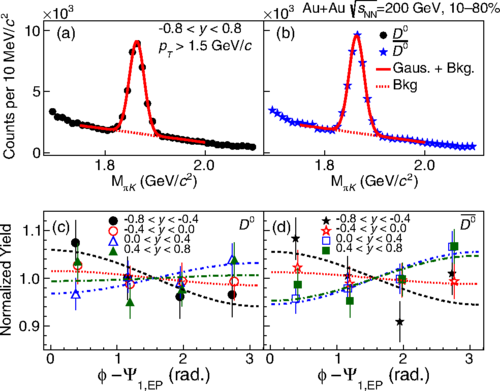
First Observation of the Directed Flow of D0 and D0 ̄ in Au+Au Collisions at sNN =200 GeV
We report the first measurement of rapidity-odd directed flow (v1) for D0 and D0̄ mesons at midrapidity (|y|
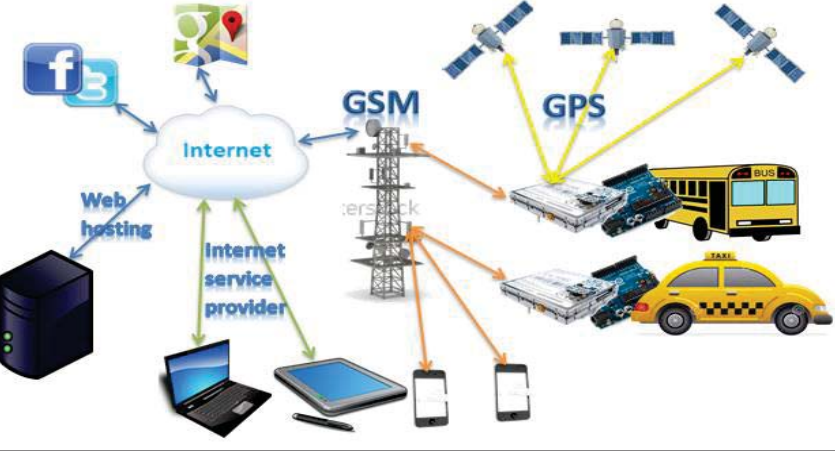
A Real-Time Social Network- Based Traffic Monitoring Vehicle Tracking System
Social networking has become an essential part of our daily lives. tTe integration of social networking communication model and Internet of Things (IoT) provides the users with a greater advantage than the benefit of using each one alone. This paper presents a real-time traffic monitoring and vehicle tracking for the public or private transportation sectors. The proposed system uses a social network service to provide traffic monitoring for individual users. A fully functional prototype model is developed and presented to demonstrate the system operation and to evaluate its performance. © 2018
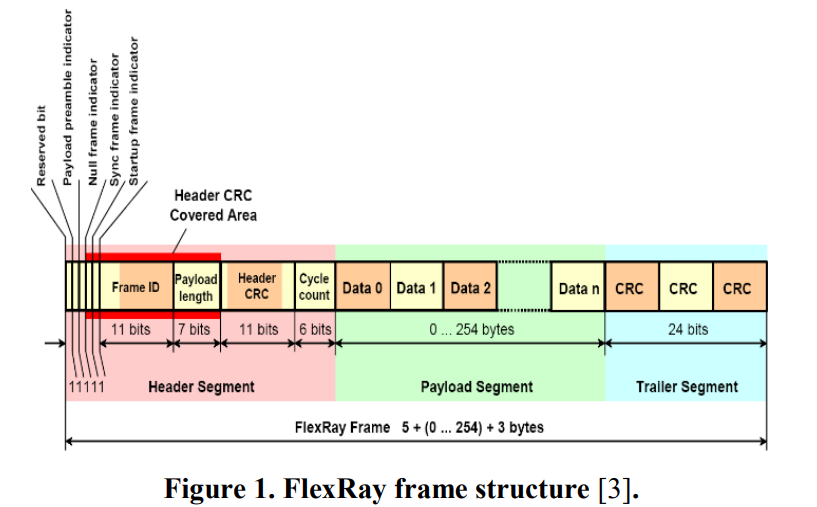
Lightweight authentication protocol deployment over FlexRay
In-vehicle network security is becoming a major concern for the automotive industry. Although there is significant research done in this area, there is still a significant gap between research and what is actually applied in practice. Controller area network (CAN) gains the most concern of community but little attention is given to FlexRay. Many signs indicate the approaching end of CAN usage and starting with other promising technologies. FlexRay is considered one of the main players in the near future. We believe that migration era is near enough to change our mindset in order to supply
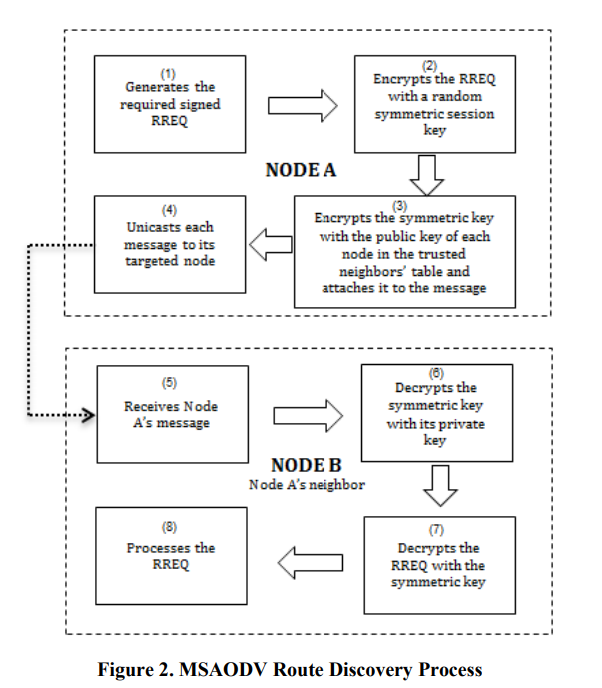
SAODV and modified SAODV performance comparison
Routing plays a vital role in ad hoc networks and Ad hoc On-demand Distance Vector (AODV) protocol is considered one of the most famous routing protocols in ad hoc networks. Unfortunately it doesn't specify security measures. This has motivated the researchers to design secured version of AODV. However Security always collides with performance. The higher the security level is, the lower the performance level. This paper presents a performance comparison between Secure AODV (SAODV) and Modified SAODV (MSAODV). © 2013 IEEE.
Pagination
- Previous page ‹‹
- Page 20
- Next page ››
