Breadcrumb
Probabilistic band-splitting for a buffered cooperative cognitive terminal
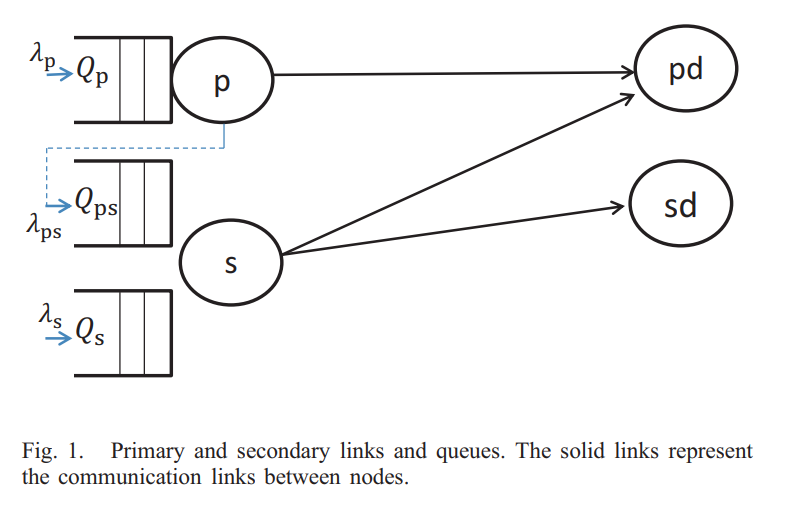
In this paper, we propose a cognitive protocol that involves cooperation between the primary and secondary users. In addition to its own queue, the secondary user (SU) has a queue to store, and then relay, the undelivered primary packets. When the primary queue is nonempty, the SU remains idle and attempts to decode the primary packet. When the primary queue is empty, the SU splits the total channel bandwidth into two orthogonal subbands and assigns each to a queue probabilistically. We show the advantage of the proposed protocol over the prioritized cognitive relaying (PCR) protocol in which
On the stable throughput of cooperative cognitive radio networks with finite relaying buffer
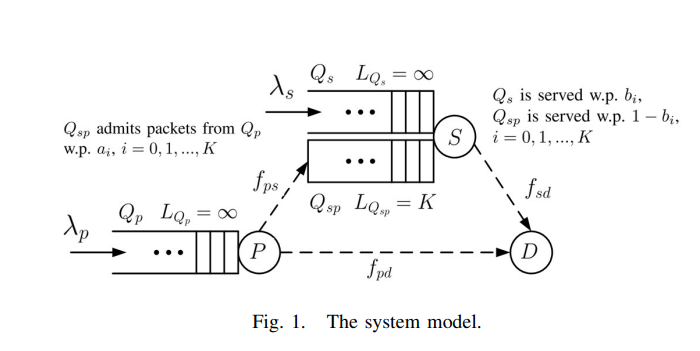
In this paper, we study the problem of cooperative communications in cognitive radio systems where the secondary user has limited relaying room for the overheard primary packets. More specifically, we characterize the stable throughput region of a cognitive radio network with a finite relaying buffer at the secondary user. Towards this objective, we formulate a constrained optimization problem for maximizing the secondary user throughput while guaranteeing the stability of the primary user queue. We consider a general cooperation policy where the packet admission and queue selection
Optimal energy allocation for delay-constrained traffic over fading multiple access channels
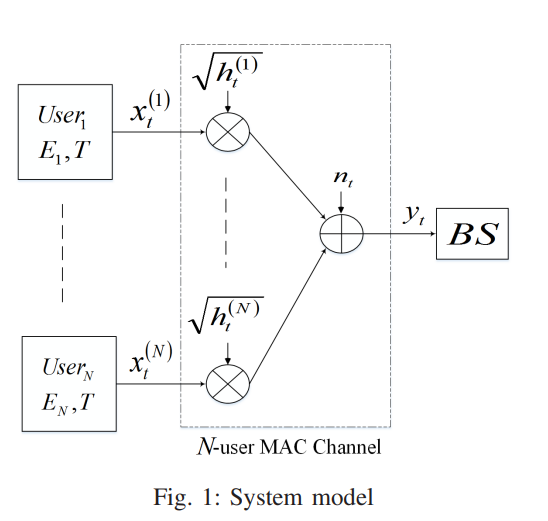
In this paper, we consider a multiple-access fading channel where N users transmit to a single base station (BS) within a limited number of time slots. We assume that each user has a fixed amount of energy available to be consumed over the transmission window. We derive the optimal energy allocation policy for each user that maximizes the total system throughput under two different assumptions on the channel state information. First, we consider the offline allocation problem where the channel states are known a priori before transmission. We solve a convex optimization problem to maximize the
RF energy harvesting in wireless networks with HARQ
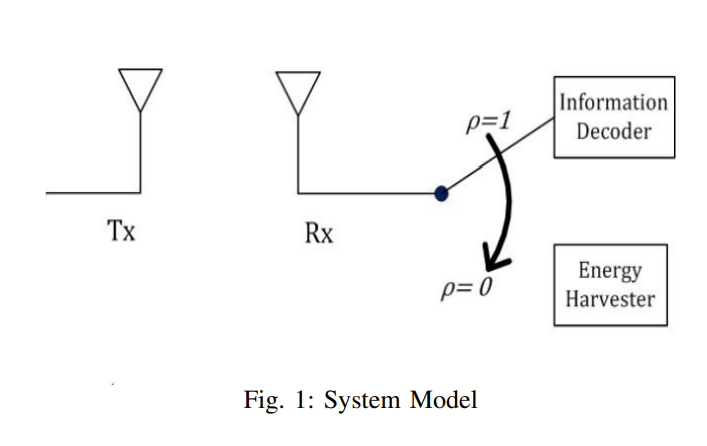
In this paper, we consider a class of wireless powered communication networks using data link layer hybrid automatic repeat request (HARQ) protocol to ensure reliable communications. In particular, we analyze the trade-off between accumulating mutual information and accumulating RF energy at the receiver of a point-to-point link using HARQ with incremental redundancy over a Rayleigh fading channel. The transmitter is assumed to have a constant energy source while the receiver relies, solely, on the RF energy harvested from the received signal. First, we target the optimal time switching (TS)
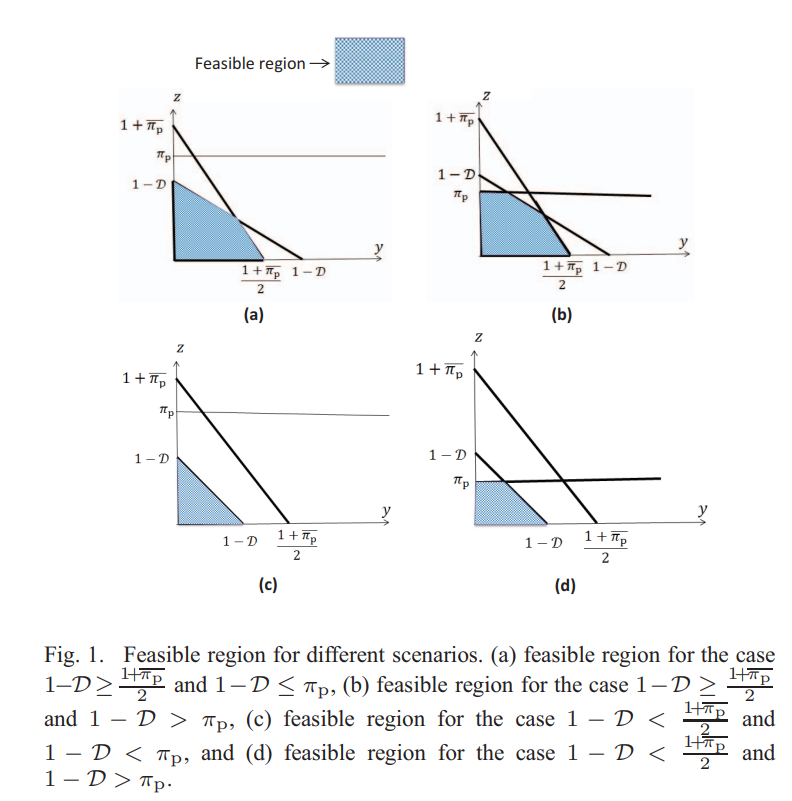
Protocol design and stability analysis of cooperative cognitive radio users
A single cognitive radio transmitter-receiver pair shares the spectrum with two primary users communicating with their respective receivers. Each primary user has a local traffic queue, whereas the cognitive user has three queues; one storing its own traffic while the other two are relaying queues used to store primary relayed packets admitted from the two primary users. A new cooperative cognitive medium access control protocol for the described network is proposed, where the cognitive user exploits the idle periods of the primary spectrum bands. Traffic arrival to each relaying queue is
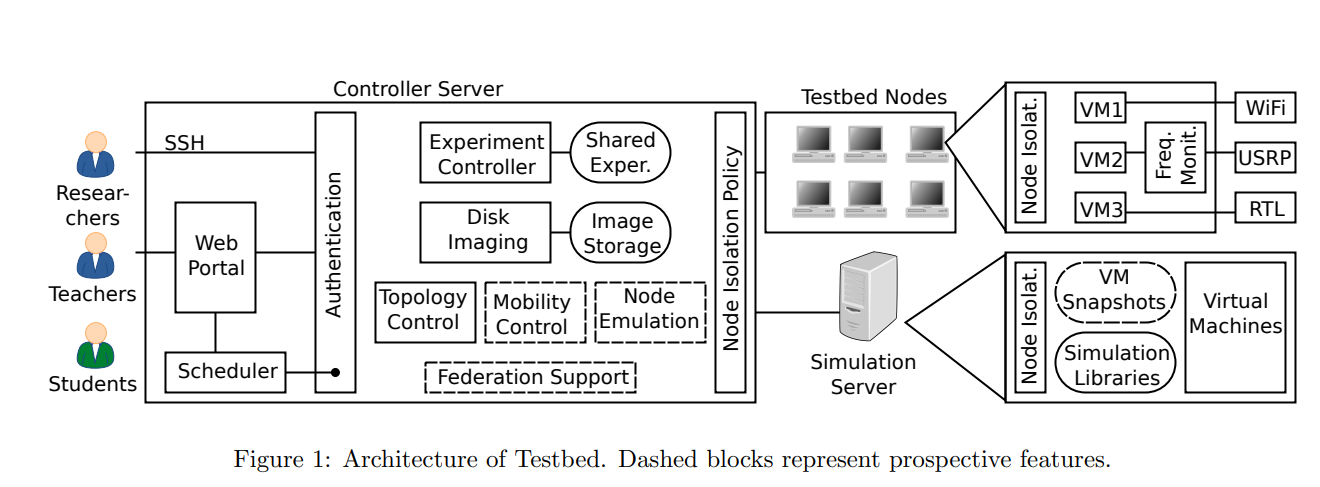
CRC: Collaborative research and teaching testbed for wireless communications and networks
The validation of wireless communications research, whether it is focused on PHY, MAC or higher layers, can be done in several ways, each with its limitations. Simulations tend to be simplified. Equipping wireless labs requires funding and time. Remotely accessible testbeds present a good option to validate research. The existing testbeds have gone a long way in building the infrastructure for managing and operating themselves. Yet, there is still space to improve the administration of resources whether it is nodes, frequency spectrum or storage space. In this work, we present the
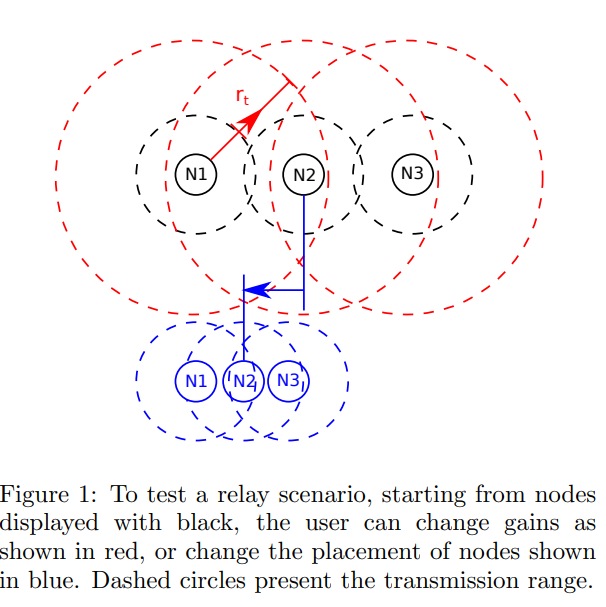
Topology realization using gain control for wireless testbeds
Wireless testbeds present a convenient and cost effective option for researchers in communications to validate their work. The main drawback of these testbeds is their reliance on nodes with fixed placement; this limits experimenters ability to test protocols that depend on a complex connectivity between the nodes such as relaying. In this work, we present a way to overcome this limitation; this method attempts to realize a given topology between a set of nodes by adjusting each node's transmit power and receive gain in a manner to connect and disconnect the links between the nodes as desired
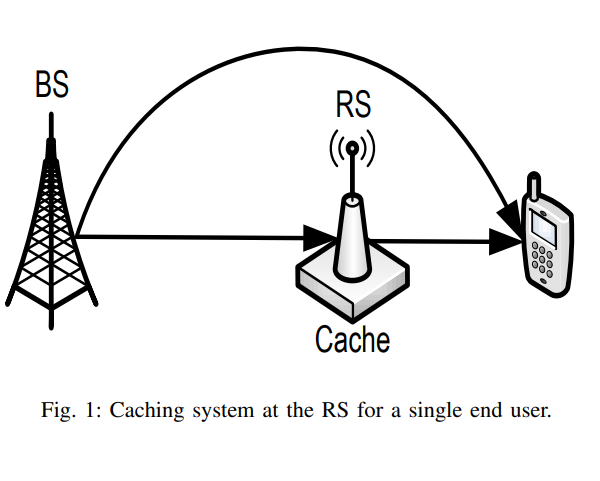
Dynamic proactive caching in relay networks
We investigate the performance of dynamic proactive caching in relay networks where an intermediate relay station caches content for potential future use by end users. A central base station proactively controls the cache allocation such that cached content remains fresh for consumption for a limited number of time slots called proactive service window. With uncertain user demand over multiple data items and dynamically changing wireless links, we consider the optimal allocation of relay stations cache to minimize the time average expected service cost. We characterize a fundamental lower

Weighted sum degrees of freedom of the asymmetric MIMO y channel with common and private messages
This paper investigates the weighted sum degrees of freedom (DoF) of the MIMO Y channel that consists of three users, where the j-Th user is equipped with Mj antennas, and a relay equipped with N antennas. In this network, each user conveys two private messages to the other two users in addition to a common message directed to both of them. As there is no direct link between the users, communication occurs through the relay. We define a weighted sum DoF metric that integrates all the network messages and weights the common message by a factor of α. Then, we study the weighted sum DoF
LTE dynamic scheduling scheme for massive M2M and H2H communication
Machine-to-Machine (M2M) has become a generally used term owing to the concept of the Internet of Things (IOT). M2M communications have numerous areas of implementation such as medicine, transportation, environmental monitoring, and smart grids. As the field of its implementation extends, the number of M2M equipment are projected to grow proportionally in the upcoming few years. Current cellular network technologies will not be able to cope with the expected increase in the number of M2M services while considering QoS as a major topic. Many applications of M2M are delay sensitive that will
Pagination
- Previous page ‹‹
- Page 20
- Next page ››
