Breadcrumb

Investigation of root causes of order unfulfillment: A Logistics case study
This study targets an order fulfillment problem in a freight forwarding company. Some applicable solutions are implemented such as supplier performance evaluation, suppliers' selection, and location analytics. The objective of the study is to reduce the number of unfulfilled orders by supply planning. Some of the tools used to achieve this are Excel (VBA and Pivot tables) to perform drivers' scoring, analytic hierarchy process (AHP), and ArcGIS software to visualize locations. The results showed that the company can implement the suggested solutions to reduce the number of order cancellations
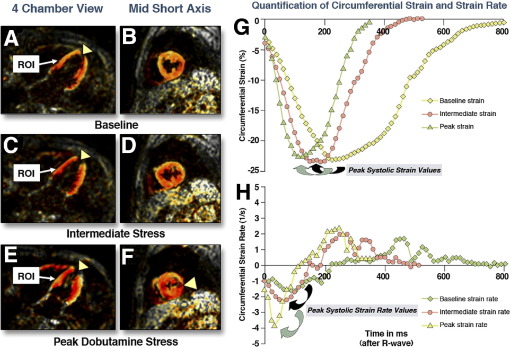
Strain-encoded CMR for the detection of inducible ischemia during intermediate stress
Objectives: This study sought to evaluate the diagnostic accuracy of strain-encoded cardiac magnetic resonance (SENC) for the detection of inducible ischemia during intermediate stress. Background: High-dose dobutamine stress cardiac magnetic resonance (DS-CMR) is a well-established modality for the noninvasive detection of coronary artery disease (CAD). However, the assessment of cine scans relies on the visual interpretation of wall motion, which is subjective, and modalities that can objectively and quantitatively assess the time course of myocardial strain response during stress are

Native Mobile Applications UI Code Conversion
With the widespread use of mobile applications in daily life, it has become crucial for software companies to develop the applications for the most popular platforms like Android and iOS. Using a native development is time consuming and costly. Cross-platform mobile development like Xamarin and React native emerged as a solution to the mentioned problem of native development for the time and cost. Meanwhile it requires the developers to learn a new language. Other tools are converting the mobile apps of specific platform to the corresponding platform, but most of them still lack the mobile
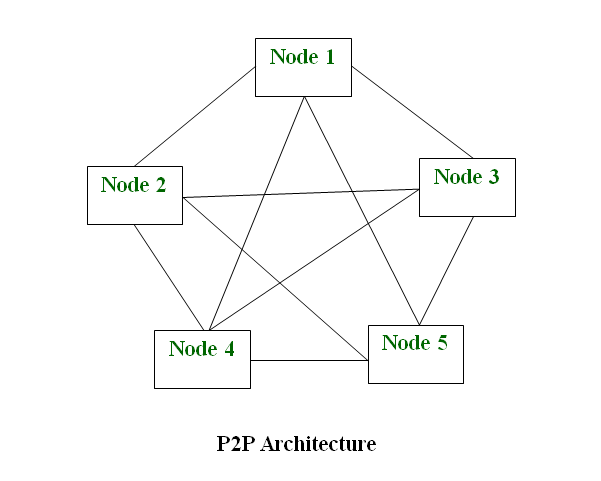
MyP2PWorld: Highly reproducible application-level emulation of P2P systems
In this paper, we describe an application-level emulator for P2P systems with a special focus on high reproducibil-ity. We achieve reproduciblity by taking control over the scheduling ofconcurrent events from the operating system. We accomplish that for inter-and intra-peer concurrency. The development ofthe system was driven by the need to enhance the testing process ofan already-developed industrial product. Therefore, we were constrained by the architecture ofthe overlying application. However, we managed to provide highly transparent emulation by wrapping standard/widely-used networking
Natcracker: Nat combinations matter
In this paper, we report our experience in working with Network Address Translators (NATs). Traditionally, there were only 4 types of NATs. For each type, the (im)possibility of traversal is well-known. Recently, the NAT community has provided a deeper dissection of NAT behaviors resulting into at least 27 types and documented the (im)possibility of traversal for some types. There are, however, two fundamental issues that were not previously tackled by the community. First, given the more elaborate set of behaviors, it is incorrect to reason about traversing a single NAT, instead combinations
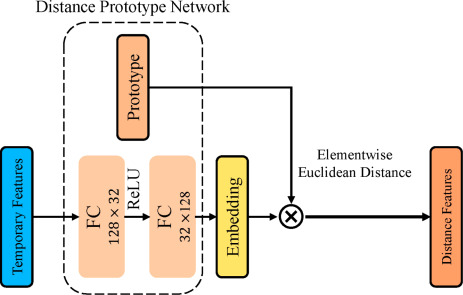
Multiple classifiers for time series classification using adaptive fusion of feature and distance based methods
Time series classification is a supervised learning problem used in many vital applications. Classification of data varying with time is considered an important and challenging pattern recognition task. The temporal aspect and lack of features in time series data makes the learning process different from traditional classification problems. In this paper we propose a multiple classifier system approach for time series classification. The proposed approach adaptively integrates extracted local and global features together with distance similarity based methods. A feature extraction process is
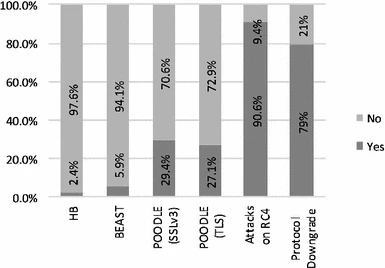
Stock exchange threat modeling, EGX as a case study
Cyber crime is a growing threat affecting all business sectors. Stock Exchanges, a financial services sector, are not far from it. Trading stocks via Internet exposes the process to cyber threats that might take advantage of a system defect to breach security and cause possible harm. Online Trading websites are protected by various security systems. Digital Certificate, which is based on Secure Socket Layer (SSL) protocol, is an example. This research examines implementation of Digital Certificate in online trading servers. This evaluation helps to identify security weaknesses and take actions
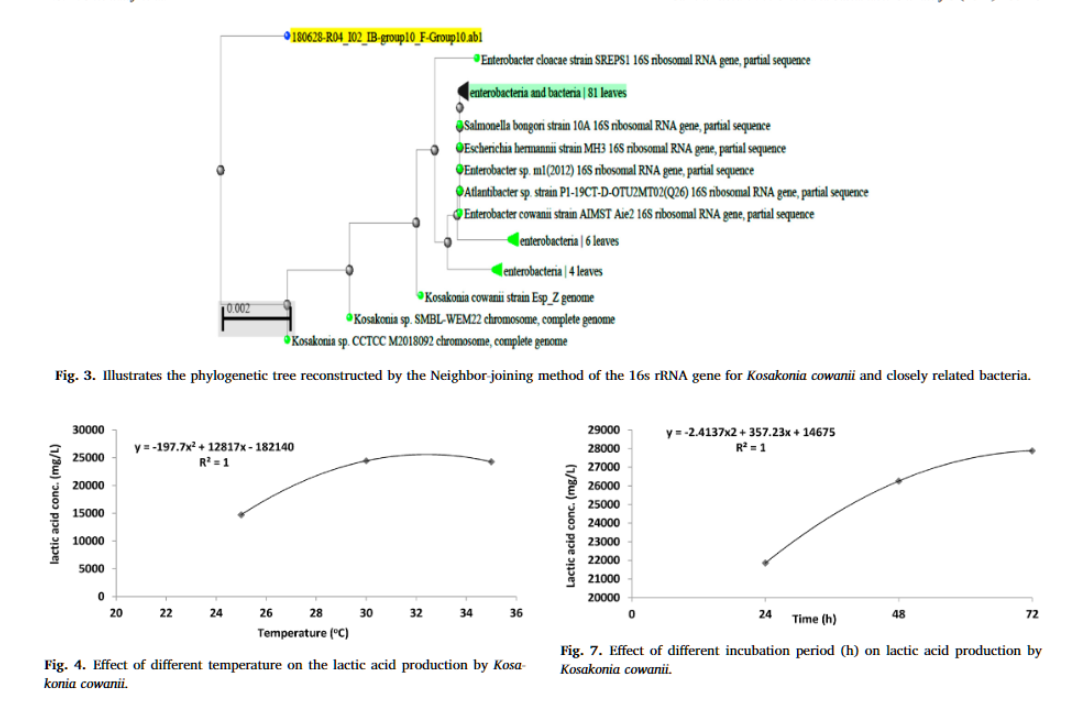
Optimization of lactic acid production from agro-industrial wastes produced by Kosakonia cowanii
Lactic acid is used for the preparation of poly-lactic acid. The objective of this research was to produce lactic acid from agro-industrial wastes as cheap, renewable substrates, and also reduce the pollution burden on the environment. Sixteen bacterial isolates were isolated from agro-industrial wastes. The chemical hydrolysis of agro-industrial wastes was achieved with hydrochloric acid, sulfuric acid, and sodium hydroxide. The highest yield of lactic acid produced was identified using 16S rRNA. The optimum conditions for lactic acid production were determined. Calcium lactate, produced from
New achievable secrecy rate regions for the two way wiretap channel
This work develops new achievable rate regions for the two way wiretap channel. In our setup, Alice and Bob wish to exchange messages securely in the presence of a passive eavesdropper Eve. In the full-duplex scenario, our achievability argument relies on allowing the two users to jointly optimize their channel prefixing distributions, such that the new channel conditions are favorable compared to that of Eve. Random binning and private key sharing over the channel are then used to exploit the secrecy advantage available in the equivalent cascade channel and to distribute the available secrecy
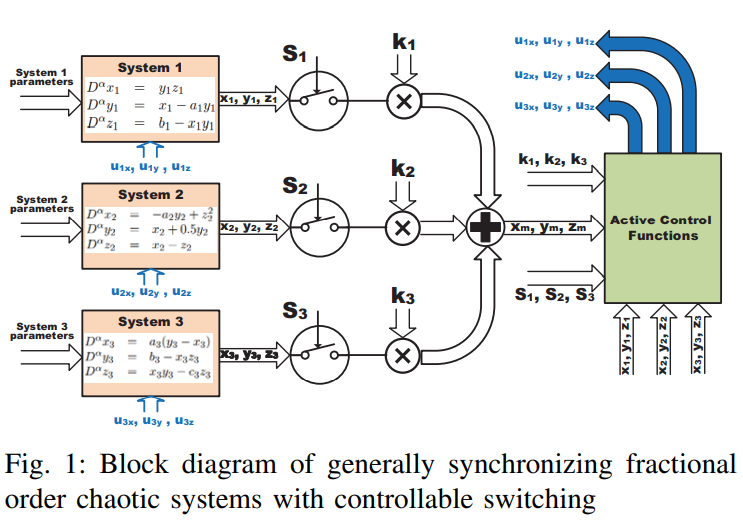
Switched active control synchronization of three fractional order chaotic systems
This paper discusses the continuous effect of fractional order parameter on two chaotic systems. Switched synchronization of three different fractional order chaotic systems is presented as an extension for synchronizing two different systems using active control. The proposed technique, which is based on the switching parameters and the scaling factors that control the choices of master and slave systems, is explained. The NonStandard Finite Difference method is used for the numerical solution of the fractional order master and slave systems. Four cases and many numeric simulations are
Pagination
- Previous page ‹‹
- Page 4
- Next page ››
